Unlocking the Secrets of Kerberos Authentication
Unlocking the Secrets of Kerberos Authentication
Kerberos, a robust authentication protocol developed at MIT, stands as a cornerstone of secure communication in distributed systems, particularly within Active Directory domains. This deep dive explores Kerberos's core functionality, key concepts, and the intricate dance of messages that ensure secure access to services across potentially insecure networks.
Understanding Kerberos Fundamentals
At its heart, Kerberos solves the problem of securely authenticating a user to a service over an untrusted network. It achieves this through mutual authentication: both the user (client) and the service verify each other's identity, ensuring the authentication messages are fresh and haven't been tampered with. This freshness is crucial; each party generates an independent challenge, encrypted with the respective private key, guaranteeing the authenticity and timeliness of the authentication.
Before we delve into the process, let's familiarize ourselves with key terms:
- Realm: A domain or group of systems where Kerberos manages authentication.
- Principal: A unique identity (user or service) within a realm.
- Client: Acts on behalf of a user to access a service.
- User: An individual within a realm.
- Service: A resource (e.g., file server, application) accessed by clients.
- Key Distribution Center (KDC): Central authority issuing tickets and session keys. Comprises:
- Authentication Server (AS): Verifies user identity, issues Ticket Granting Tickets (TGTs).
- Ticket Granting Server (TGS): Verifies access requests, issues Service Tickets.
- Authenticators: Records (with timestamps) generated using the client-server session key.
- Tickets: Encrypted data (service keys, timestamps, client identifiers) encrypted with the service's secret key.
The Kerberos Authentication Flow
Let's walk through the steps of Kerberos authentication. The diagram below visually illustrates these exchanges:
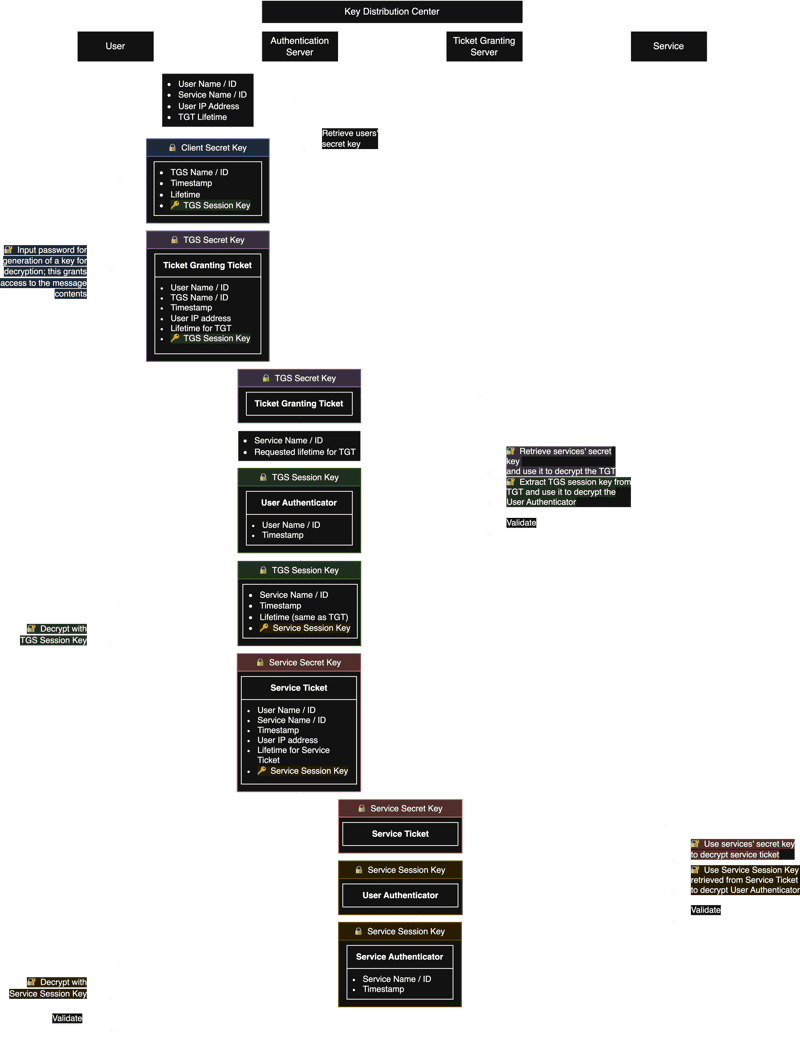
The Kerberos Flow. A higher resolution version can be downloaded here. Based on this video.
- Client Initialization: The client initiates communication with the AS (Authentication Server) via an unencrypted message containing the client's identity and the requested service.
- AS Response: The AS authenticates the client and responds with a TGT (Ticket Granting Ticket) and a session key encrypted with the client's secret key. This session key is essential for subsequent communications.
- Client to TGS Request: The client decrypts the AS response, obtains the session key, and uses it to create a request to the TGS (Ticket Granting Server). This request includes the TGT received in step 2.
- TGS Response: The TGS validates the TGT and, upon successful verification, grants a Service Ticket for the requested service. This ticket is encrypted with the service's secret key.
- Client to Service Request: The client decrypts the Service Ticket. Along with this ticket, the client sends an authenticator (containing a timestamp encrypted with the session key) to the service.
- Service Authentication: The service uses its secret key to decrypt the Service Ticket, verifying the client's identity. The service then typically sends its own response, completing the mutual authentication process.
Conclusion
Kerberos, despite its complexity, provides a robust and secure solution for authentication in distributed environments. Understanding its core components and the authentication flow is critical for anyone working with networked systems, particularly those involving Active Directory. This detailed explanation should serve as a foundational understanding for further exploration into this vital security mechanism.
References
- B. Neuman and T. Ts’o, "Kerberos: an authentication service for computer networks," IEEE Communications Magazine, vol. 32, no. 9, pp. 33–38, Sep. 1994. [Online](https://ieeexplore.ieee.org/document/312841/?arnumber=312841)
- J. G. Steiner, C. Neuman, and J. I. Schiller, "Kerberos: An Authentication Service for Open Network Systems," 1988.
- D. Otway and O. Rees, "Efficient and timely mutual authentication," ACM SIGOPS Operating Systems Review, vol. 21, no. 1, pp. 8–10, Jan. 1987. [Online](https://dl.acm.org/doi/10.1145/24592.24594)
- Destination Certification, "Kerberos Authentication Explained | A deep dive," Apr. 2020. [Online](https://youtu.be/5N242XcKAsM)
Related Articles
Software Development
Unveiling the Haiku License: A Fair Code Revolution
Dive into the innovative Haiku License, a game-changer in open-source licensing that balances open access with fair compensation for developers. Learn about its features, challenges, and potential to reshape the software development landscape. Explore now!
Read MoreSoftware Development
Leetcode - 1. Two Sum
Master LeetCode's Two Sum problem! Learn two efficient JavaScript solutions: the optimal hash map approach and a practical two-pointer technique. Improve your coding skills today!
Read MoreBusiness, Software Development
The Future of Digital Credentials in 2025: Trends, Challenges, and Opportunities
Digital credentials are transforming industries in 2025! Learn about blockchain's role, industry adoption trends, privacy enhancements, and the challenges and opportunities shaping this exciting field. Discover how AI and emerging technologies are revolutionizing identity verification and workforce management. Explore the future of digital credentials today!
Read MoreSoftware Development
Unlocking the Secrets of AWS Pricing: A Comprehensive Guide
Master AWS pricing with this comprehensive guide! Learn about various pricing models, key cost factors, and practical tips for optimizing your cloud spending. Unlock significant savings and efficiently manage your AWS infrastructure.
Read MoreSoftware Development
Exploring the GNU Verbatim Copying License
Dive into the GNU Verbatim Copying License (GVCL): Understand its strengths, weaknesses, and impact on open-source collaboration. Explore its unique approach to code integrity and its relevance in today's software development landscape. Learn more!
Read MoreSoftware Development
Unveiling the FSF Unlimited License: A Fairer Future for Open Source?
Explore the FSF Unlimited License: a groundbreaking open-source license designed to balance free software distribution with fair developer compensation. Learn about its origins, strengths, limitations, and real-world impact. Discover how it addresses the challenges of open-source sustainability and innovation.
Read MoreSoftware Development
Conquer JavaScript in 2025: A Comprehensive Learning Roadmap
Master JavaScript in 2025! This comprehensive roadmap guides you through fundamental concepts, modern frameworks like React, and essential tools. Level up your skills and build amazing web applications – start learning today!
Read MoreBusiness, Software Development
Building a Successful Online Gambling Website: A Comprehensive Guide
Learn how to build a successful online gambling website. This comprehensive guide covers key considerations, technical steps, essential tools, and best practices for creating a secure and engaging platform. Start building your online gambling empire today!
Read MoreAI, Software Development
Generate Images with Google's Gemini API: A Node.js Application
Learn how to build an AI-powered image generator using Google's Gemini API and Node.js. This comprehensive guide covers setup, API integration, and best practices for creating a robust image generation service. Start building today!
Read MoreSoftware Development
Discover Ocak.co: Your Premier Online Forum
Explore Ocak.co, a vibrant online forum connecting people through shared interests. Engage in discussions, share ideas, and find answers. Join the conversation today!
Read MoreSoftware Development
Mastering URL Functions in Presto/Athena
Unlock the power of Presto/Athena's URL functions! Learn how to extract hostnames, parameters, paths, and more from URLs for efficient data analysis. Master these essential functions for web data processing today!
Read MoreSoftware Development
Introducing URL Opener: Open Multiple URLs Simultaneously
Tired of opening multiple URLs one by one? URL Opener lets you open dozens of links simultaneously with one click. Boost your productivity for SEO, web development, research, and more! Try it now!
Read More
Software Development, Business
Unlocking the Power of AWS: A Deep Dive into Amazon Web Services
Dive deep into Amazon Web Services (AWS)! This comprehensive guide explores key features, benefits, and use cases, empowering businesses of all sizes to leverage cloud computing effectively. Learn about scalability, cost-effectiveness, and global infrastructure. Start your AWS journey today!
Read MoreSoftware Development
Understanding DNS in Kubernetes with CoreDNS
Master CoreDNS in Kubernetes: This guide unravels the complexities of CoreDNS, Kubernetes's default DNS server, covering configuration, troubleshooting, and optimization for seamless cluster performance. Learn best practices and avoid common pitfalls!
Read MoreSoftware Development
EUPL 1.1: A Comprehensive Guide to Fair Open Source Licensing
Dive into the EUPL 1.1 open-source license: understand its strengths, challenges, and real-world applications for fair code. Learn how it balances freedom and developer protection. Explore now!
Read MoreSoftware Development
Erlang Public License 1.1: Open Source Protection Deep Dive
Dive deep into the Erlang Public License 1.1 (EPL 1.1), a crucial open-source license balancing collaboration and contributor protection. Learn about its strengths, challenges, and implications for developers and legal teams.
Read MoreSoftware Development
Unlocking Kerala's IT Job Market: Your Path to Data Science Success
Launch your data science career in Kerala's booming IT sector! Learn the in-demand skills to land high-paying jobs. Discover top data science courses & career paths. Enroll today!
Read More
Software Development
Automation in Software Testing: A Productivity Booster
Supercharge your software testing with automation! Learn how to boost productivity, efficiency, and accuracy using automation tools and best practices. Discover real-world examples and get started today!
Read MoreSoftware Development
Mastering Anagram Grouping in JavaScript
Master efficient anagram grouping in JavaScript! Learn two proven methods: sorting and character counting. Optimize your code for speed and explore key JavaScript concepts like charCodeAt(). Improve your algorithms today!
Read More
Software Development
Mastering Kubernetes Deployments: Rolling Updates and Scaling
Master Kubernetes Deployments for seamless updates & scaling. Learn rolling updates, autoscaling, and best practices for high availability and efficient resource use. Improve your application management today!
Read More